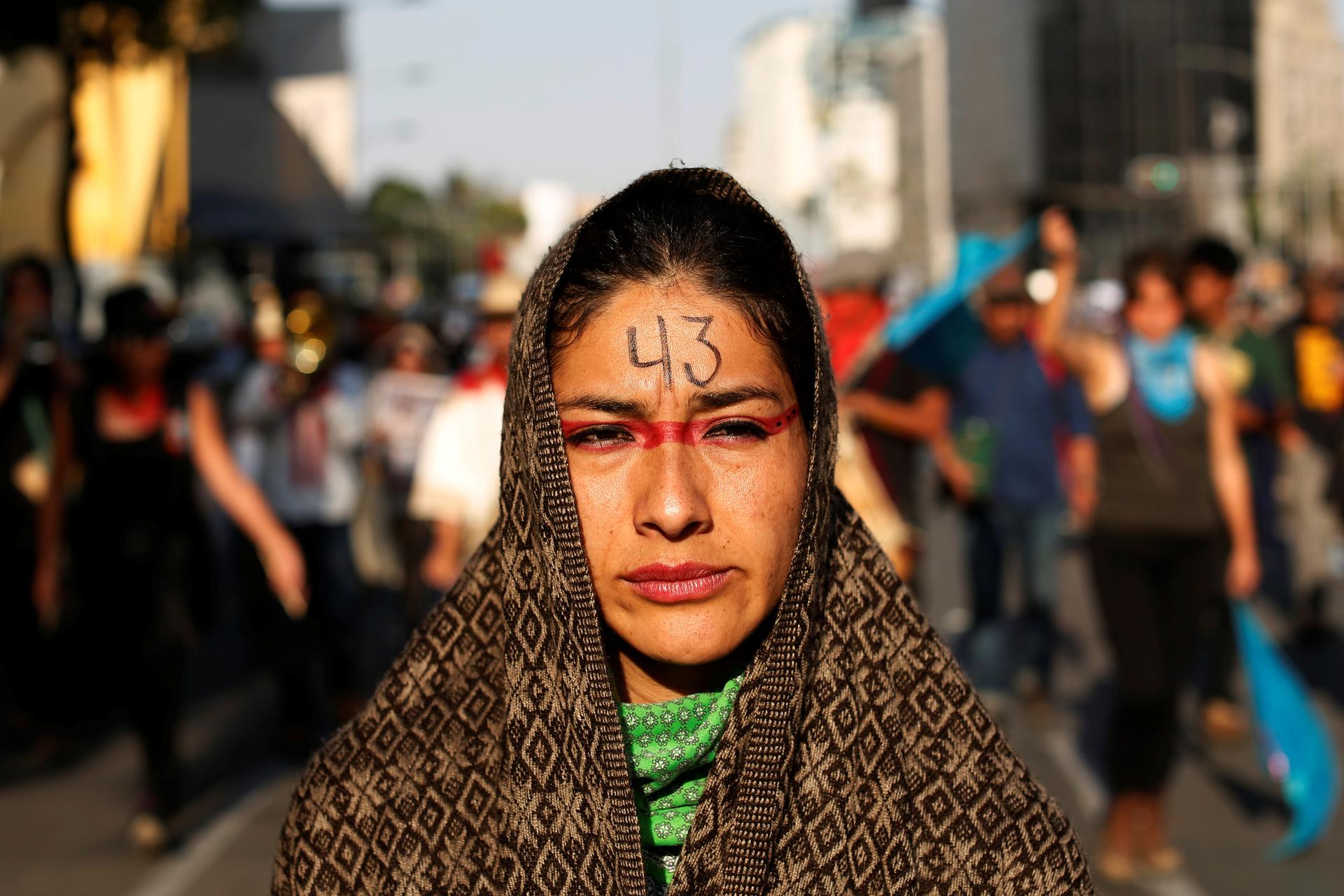A woman takes part in a march to mark the anniversary of the disappearance of the 43 students of Ayotzinapa College Raul Isidro Burgos in the state of Guerrero in Mexico City on Feb. 26, 2017.
International experts investigating the disappearance of 43 students in Mexico in 2014 were targeted with spyware sold to the government, cybersecurity experts said this week.
Adding to a snowballing scandal over spying on journalists, activists and other public figures in Mexico, computer security experts confirmed that the independent investigation into the disappearance and alleged massacre — an atrocity that drew worldwide condemnation — was targeted with highly invasive spyware known as Pegasus.
"The infection attempts took place in early March of 2016, shortly after the [independent experts] had criticized the Mexican government for interference in their investigation, and as they were preparing their final report," said researchers at The Citizen Lab at the University of Toronto.
The revelation effectively unites two of the biggest scandals of President Enrique Peña Nieto's administration — the illegal spying allegations and the lingering stain of the missing students — at a time when his party, the long-dominant Institutional Revolutionary Party, risks losing power in a presidential election next year.
Mexico is still haunted by the mystery of the 43 missing students, who were abducted by corrupt police in September 2014 in the southern city of Iguala.
Prosecutors initially said the officers delivered the students to drug cartel hitmen who killed them and burned their bodies — allegedly to stop them from staging a planned protest.
But the independent experts sent by the Washington-based Inter-American Commission on Human Rights rejected that version of events.
They demanded further investigation, and suggested the students may have been killed for unwittingly hijacking buses carrying heroin or drug money, possibly linked to someone in power.
Their investigation was shut down when the government declined to renew their mandate.
'Systematic abuse'
Citizen Lab previously found the same spyware was used to target the phones of leading journalists, anti-corruption activists, human rights campaigners and opposition politicians.
Based on those findings, nine victims have pressed charges against the government, accusing it of violating their privacy with a tool meant to be used to fight terrorists and criminals.
The government denies the charges and has ordered the attorney general's office to investigate.
But victims have condemned the probe as a whitewash, pointing out that the attorney general's office is itself one of the government bodies that purchased the spyware.
No one from the Mexican government has contacted Citizen Lab for information about its findings, said John Scott-Railton, senior researcher at the lab and the lead author on the spying studies.
He called the scope of the spying in Mexico unprecedented.
"What we have shown is systematic abuse of this technology, more so than we've ever seen in any case we have examined in the past half-decade of tracking this industry," he told AFP.
He said he could not prove whether the spying was carried out by the government, but that whoever was behind it was "extremely motivated to target critics of the government and others who challenged the government's positions on a wide range of issues."
But the spying on the international body takes the scandal one step further. In the past, the surveillance campaign targeted domestic critics of the government. But this case shows that international officials who were granted a status like diplomatic immunity were also targeted.
"We had a document that showed we had immunity from criminal prosecution and searches and seizures," says Francisco Cox, a Chilean human rights lawyer and one of the investigators. "For example, any time I went into Mexico, and left Mexico, [security officials] could not take my luggage."
Cox says that if international officials with immunity can be targeted, what about those without similar protections? "We don't know if it's the government … but If whoever is spying has the audacity to spy on a group that is an international body with diplomatic immunity, then what common citizens are exposed to is pretty fearsome."
'Spy in your pocket'
The Pegasus spyware effectively turns a target's cellphone into a "spy in your pocket," enabling remote access to the user's data, camera and microphone, said Scott-Railton.
It is made by a secretive Israeli firm called NSO Group, owned by US private equity firm Francisco Partners Management.
Citizen Lab says it has now documented 19 cases of spying or attempted spying on investigative journalists, anti-corruption activists, human rights campaigners, opposition politicians and public health advocates.
The targets all reported receiving text messages with eye-catching news headlines, social media posts or personal communications.
In the case of the independent experts investigating the 43 missing students, the main cellphone they were using in Mexico received messages relating to the death of someone's father and purportedly linking to details on the funeral.
"We thought it was a death threat," says Cox. But then once members of the group started to suspect they've been spied on, they sent the text message to Citizen Lab.
In reality, the link pointed to a site set up to install Pegasus on targets' phones, says Citizen Lab.
The president of the Inter-American Commission on Human Rights, Francisco Eguiguren, condemned the spyware targeting as "extremely troubling" and called for an independent investigation.
Information from Agence France-Presse was used in this report.